-
Open the Web Service Setup page on the Server and the Client.
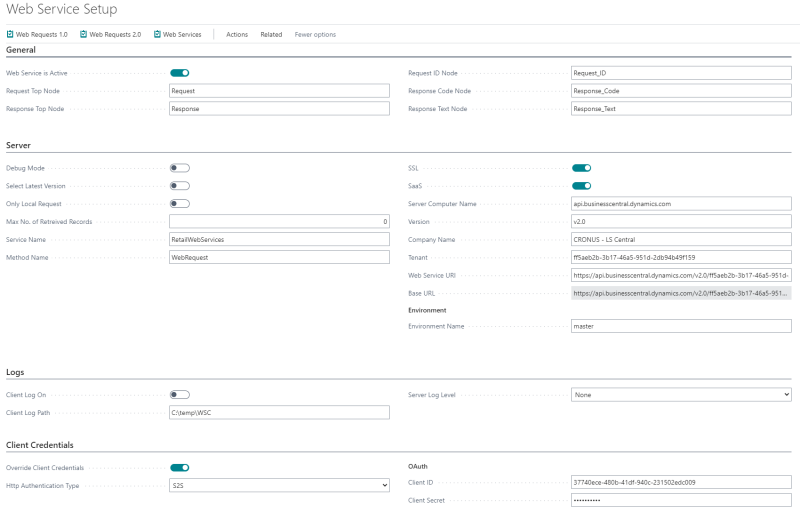
- Enable SSL, if the server URL is https.
- Enable SaaS because the server is running on SaaS.
- Fill in all fields as in the above image.
- In the Client Credentials FastTab, enable Override Client Credentials and change Http Authentication Type to S2S.
- In the Client ID field, enter the App ID that you created on the Azure portal (see How to: Set Up an Azure Active Directory App).
- Go to the Web Requests 2.0 page, and click the Publisher action on the server and the Subscriber action on the client.
- Go to the POS Functionality Profile List, and select the profile you want to change (for example ##DEFAULT).
- On the POS Functionality Profile Card, click the Profile action and then Web Servers.
- Clear the Local Request check box, and select the distribution location.
- Back on the Profile Card, in the Web Services FastTab, enable Distribution Location in the Send Transactions section.
- Open the Distribution Location Card, for example for HO.
- In the Web Server FastTab, add the same information as in the web service setup.
The POS will now send requests to the Server on SaaS, and will authenticate using OAuth 2.0.
Troubleshooting
User permission
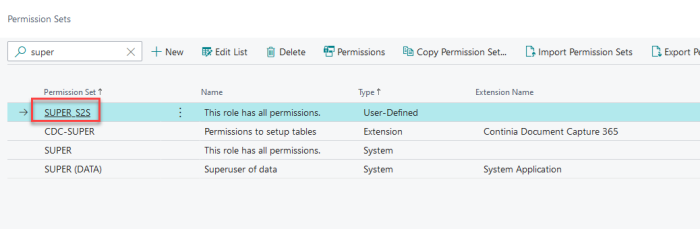
The user must have sufficient permission. The best way to start is to assign the user with a SUPER equivalent permission set, because at this point you do not know which objects the permission set must have.
The super user permission set cannot be assigned to this user, so you must create a new permission set based on the SUPER permission set.
- Create a new Permission Set, name it Super_S2S, for example.
- Copy the existing super permission set, and assign that to the S2S user.
- You can refine this permission set, if needed.
Company names with empty space
When you create the web service URL in Web Service Setup, for company names with a blank space in it, like LS Retail for example, replace the space with %20 to avoid creating an incorrect URL. The correctly entered company name now reads LS%20Retail instead.
The following is a PowerShell script that you can use to test the S2S setup:
########################## Variables to update#########################$clientid = ""$clientsecret = ""$tenant = ""$environmentName = ""$companyName = ""
########################## Other variables#########################
# Get access token$body = @{grant_type="client_credentials";scope=$scope;client_id=$ClientID;client_secret=$ClientSecret}$oauth = Invoke-RestMethod -Method Post -Uri $("https://login.microsoftonline.com/$tenant/oauth2/v2.0/token") -Body $body$oauth.access_token
# Get companies$companies = Invoke-RestMethod `-Method Get `-Uri $("$baseurl/api/v2.0/companies") `-Headers @{Authorization='Bearer ' + $oauth.access_token}foreach ($company in $companies.value) {$company.id + " - " + $company.displayName}
This way you should get the list of companies.
Tip: To test the web services connection, you can run these lines:
# Test WS connection$ws_url = "$baseurl/WS/$companyName/Codeunit/TestConnection"$headers = @{"Authorization" = "Bearer " + $oauth.access_token}$response = Invoke-WebRequest -UseBasicParsing `-Method Post `-Uri $("$ws_url") `-Headers $headers$response
500 - Internal Server Error
If you get this error message, 500 - Internal Server Error, when you click the Subscriber action on the Web Service Setup page, you most likely have a user permissions issue.
Check the user setup in the Azure Active Directory Application Card, and make sure it has the proper permissions.
To check the failure reason, you can run these lines:
# Test Web Services subscriptiontry{$ws_url = "$baseurl/WS/$companyName/Codeunit/RetailMessageGetActiveList"$headers = @{"Authorization" = "Bearer " + $oauth.access_token}$response = Invoke-WebRequest -UseBasicParsing `-Method Post `-Uri $("$ws_url") `-Headers $headers$response}catch {$reader = New-Object System.IO.StreamReader($_.Exception.Response.GetResponseStream())$reader.BaseStream.Position = 0$reader.DiscardBufferedData()$reader.ReadToEnd()}
Common issues
Response: <s:Envelope xmlns:s="http://schemas.xmlsoap.org/soap/envelope/"><s:Body><s:Fault><faultcode xmlns:a="urn:microsoft-dynamics-schemas/error">a:Microsoft.Dynamics.Nav.Service.SOAP.ServiceBrokerException</faultcode><faultstring xml:lang="en-US">Service "Codeunit/RetailMessageGetActiveList" was not found!</faultstring><detail><string xmlns="http://schemas.microsoft.com/2003/10/Serialization/">Service "Codeunit/RetailMessageGetActiveList" was not found!</string></detail></s:Fault></s:Body></s:Envelope>
Reason: The user configured in the Azure Active Directory Application Card don't have proper permissions (review the setup).
Response: <s:Envelope xmlns:s="http://schemas.xmlsoap.org/soap/envelope/"><s:Body><s:Fault><faultcode xmlns:a="urn:microsoft-dynamics-schemas/error">a:Microsoft.Dynamics.Nav.Types.NavPermissionException</faultcode><faultstring xml:lang="en-US">You do not have the following permissions on XmlPort LSCRetailMSGGetActiveListXML: Execute.
To view details about your permissions, see the Effective Permissions page.
To report a problem, refer to the following server session ID: '42060'.</faultstring><detail><string xmlns="http://schemas.microsoft.com/2003/10/Serialization/">You do not have the following permissions on XmlPort LSCRetailMSGGetActiveListXML: Execute.
To view details about your permissions, see the Effective Permissions page.
To report a problem, refer to the following server session ID: '42060'.</string></detail></s:Fault></s:Body></s:Envelope>
Reason: The user is not configured in the Azure Active Directory Application Card and does not have the proper permissions or consent was not granted (check Troubleshooting - User permissions).
Multi-tenant setup
Note: The application and Business Central must be on the same AAD (Azure Active Directory). They can be on different tenants, but setup only works if they are both in the same AAD.
See also
Video Tutorial: S2S Authentication - Step 3.1
Video Tutorial: S2S Authentication - Step 3.2